时间:2024-04-15|浏览:340
As the crypto market becomes more and more popular, Web3 projects and gameplay are changing at a very fast pace, and players' emotions are getting more and more excited. As a result, players accidentally step into traps and get stolen or phished while participating in various new projects. In this context, combined with the information we have collected on and off the chain, we hope to expand a series of practical examples closely related to the security of user assets, so we have the Web3 Security Beginner's Guide to Avoiding Pitfalls.
We plan to integrate the risk points in the Web3 field as comprehensively as possible, and use examples as a background to help readers better identify and prevent risks. The main contents of this guide include but are not limited to: risks in the process of downloading and using wallets; pitfalls that may fall into when participating in various Web3 ecological projects; how to better identify whether signature authorization is dangerous; how to remedy it after it is unfortunately stolen, etc. (Ps. The content is tentative, and the plan cannot keep up with the changes in reality and the editor's ideas, so the final content may be more or less than planned)
Whether you are a beginner who wants to explore the unknown and novel world of Web3, but is overwhelmed by industry jargon, gameplay different from Web2, and unknown risks; or you are an old player of Web3, who has been trekking in the dark forest of blockchain for a while, has heard of and seen many "pitfalls", or even stepped on them, but is not very clear about the reasons for theft and how to avoid being damaged again, you can learn this pit avoidance guide with us. This guide aims to enable every user to better protect their assets and go further in the dark forest of blockchain.
As we all know, wallets are the entrance to the crypto world and the infrastructure of Web3, and their importance is self-evident. So without further ado, let’s introduce the first “appetizer” - wallet classification and risks.
Browser wallets such as MetaMask, Rabby, etc. are installed as browser plug-ins in the user's browser (such as Google Chrome, Firefox, etc.). Browser wallets are usually easier to access and use, and do not require downloading or installing additional software.
(https://metamask.io/download/)
Web wallets allow users to access and manage crypto assets through a web browser. Although this method is more convenient, the risks behind it cannot be ignored. Web wallets generally encrypt mnemonics and store them in the browser's local storage, so they may be threatened by malware or network attacks.
(https://www.myetherwallet.com/wallet/access/software?type=overview)
Mobile wallets work similarly to their web counterparts and are usually available as apps that users can download and install on their phones.
(https://token.im/download?locale=en-us)
Desktop wallets were more common in the early days of cryptocurrency, and well-known ones include Electrum, Sparrow, etc. This type of wallet is an application installed on a computer, and private keys and transaction data are stored on the user's local device. The user has full control over his or her cryptocurrency private key.
(https://sparrowwallet.com/)
Hardware wallets are physical devices used to store cryptocurrencies and digital assets, such as Trezor, imKey, Ledger, Keystone, OneKey, etc. Hardware wallets provide a way to store private keys offline, which means that when using hardware wallets to interact with DApps, private keys will not be exposed online.
(https://shop.ledger.com/products/ledger-nano-s-plus/matte-black)
A paper wallet is a cryptocurrency address and its private key printed on a piece of paper in the form of a QR code, and then cryptocurrency transactions are carried out by scanning the QR code.
(https://www.walletgenerator.net/?culture=zh¤cy=bitcoin)
Since many mobile phones do not support Google Play or because of network problems, many people will download wallets from other channels, such as third-party download sites, or directly search for a wallet with a browser, and then randomly click on a top-ranked link. In this way, there is a high probability that a fake wallet will be downloaded, because search engine advertising space and natural traffic can be purchased. Scammers can forge a fake wallet official website by purchasing top-ranked advertising space to trick users into visiting. The following figure shows the results of searching for TP wallet using Baidu:
(https://mp.weixin.qq.com/s/NdwIE412MJ7y-O5f2OrSHA)
Supply chain attacks are one of the main threats to hardware wallet security. If the user does not purchase a hardware wallet from an official store or authorized dealer, it is uncertain how many hands the wallet will pass through before it reaches the user, and whether the internal components have been tampered with. In the picture below, the hardware wallet on the right has been tampered with.
(https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/)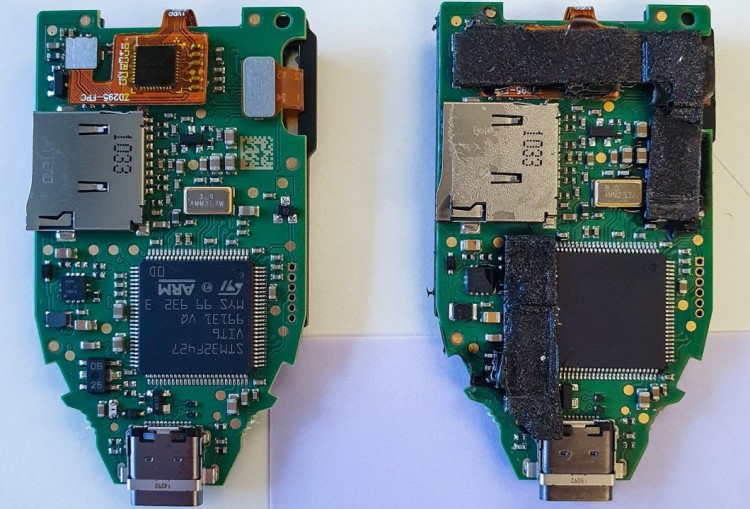
If the computer is infected with a Trojan, the wallet will be affected by the malware. The SlowMist Security Team has written an article about the Redline Stealer Trojan that analyzes the formation process and impact of the risk in detail. Interested readers can click to view it. We recommend that users install antivirus software, such as Kaspersky, AVG, 360, etc., keep the real-time protection of the security software turned on, and update the latest virus database at any time.
Finally, you may have downloaded a genuine wallet, used it carefully, and the device and real environment are safe enough, but if there is a problem with the design of the wallet itself, it may also be attacked by hackers, and the users of the wallet will also suffer asset losses. This is why when choosing a wallet, you cannot only consider the convenience of the wallet, but also whether the wallet code is open source. External developers and auditors can find potential vulnerabilities through open source code and reduce the possibility of wallet attacks. Even if the wallet is unfortunately stolen due to a vulnerability, security personnel can quickly locate the vulnerability and remedy it in time.
In this issue, we mainly introduced the classification of wallets and listed common risk points to help readers form a basic concept of wallet security. No matter which type or brand of wallet you choose, you should always keep the mnemonic and private key confidential and secure. You can consider integrating the advantages of different types of wallets and using multiple types of wallets together, such as using a combination of well-known hardware wallets + well-known software wallets to manage heavy assets, and using multiple well-known software wallets to manage light assets in a decentralized manner. In the next issue, we will introduce the pitfalls of downloading and purchasing wallets in detail, and welcome to follow us. (Ps. The wallet brands and pictures mentioned in this article are only for the purpose of assisting readers' understanding and do not constitute recommendations or guarantees)